Integrating Microsoft Identity Platform with a Python web application
About this sample
This sample is also available as a quickstart for the Microsoft identity platform: Quickstart: Add sign-in with Microsoft to a Python web app
Overview
This sample demonstrates a Python web application that signs-in users with the Microsoft identity platform and calls the Microsoft Graph.
- The python web application uses the Microsoft Authentication Library (MSAL) to obtain a JWT access token from the Microsoft identity platform (formerly Azure AD v2.0):
- The access token is used as a bearer token to authenticate the user when calling the Microsoft Graph.
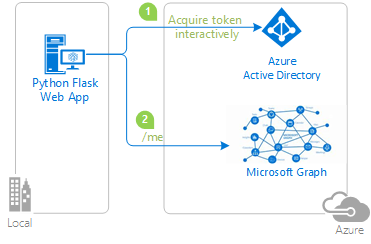
Scenario
This sample shows how to build a Python web app using Flask and MSAL Python, that signs in a user, and get access to Microsoft Graph. For more information about how the protocols work in this scenario and other scenarios, see Authentication Scenarios for Azure AD.
How to run this sample
To run this sample, you’ll need:
- Python 2.7+ or Python 3+
- An Azure Active Directory (Azure AD) tenant. For more information on how to get an Azure AD tenant, see how to get an Azure AD tenant.
Step 1: Clone or download this repository
From your shell or command line:
git clone https://github.com/Azure-Samples/ms-identity-python-webapp.git
or download and extract the repository .zip file.
Given that the name of the sample is quite long, you might want to clone it in a folder close to the root of your hard drive, to avoid file name length limitations when running on Windows.
Step 2: Register the sample application with your Azure Active Directory tenant
There is one project in this sample. To register it, you can:
- either follow the steps Step 2: Register the sample with your Azure Active Directory tenant and Step 3: Configure the sample to use your Azure AD tenant
- or use PowerShell scripts that:
- automatically creates the Azure AD applications and related objects (passwords, permissions, dependencies) for you
- modify the applications’ configuration files.
If you want to use this automation:
- On Windows, run PowerShell and navigate to the root of the cloned directory
-
In PowerShell run:
Set-ExecutionPolicy -ExecutionPolicy RemoteSigned -Scope Process -Force - Run the script to create your Azure AD application and configure the code of the sample application accordingly.
-
In PowerShell run:
cd .\AppCreationScripts\ .\Configure.ps1 cd ..Other ways of running the scripts are described in App Creation Scripts
If you don’t want to use this automation, follow the steps below.
Choose the Azure AD tenant where you want to create your applications
As a first step you’ll need to:
- Sign in to the Azure portal using either a work or school account or a personal Microsoft account.
- If your account is present in more than one Azure AD tenant, select your profile at the top right corner in the menu on top of the page, and then switch directory. Change your portal session to the desired Azure AD tenant.
Register the Python Webapp (python-webapp)
- Navigate to the Microsoft identity platform for developers App registrations page.
- Select New registration.
- When the Register an application page appears, enter your application’s registration information:
- In the Name section, enter a meaningful application name that will be displayed to users of the app, for example
python-webapp. - Change Supported account types to Accounts in any organizational directory and personal Microsoft accounts (e.g. Skype, Xbox, Outlook.com).
- In the Redirect URI (optional) section, select Web in the combo-box and enter the following redirect URIs:
http://localhost:5000/getAToken.
- In the Name section, enter a meaningful application name that will be displayed to users of the app, for example
- Select Register to create the application.
- On the app Overview page, find the Application (client) ID value and record it for later. You’ll need it to configure the Visual Studio configuration file for this project.
- Select Save.
-
From the Certificates & secrets page, in the Client secrets section, choose New client secret:
- Type a key description (of instance
app secret), - Select a key duration of either In 1 year, In 2 years, or Never Expires.
- When you press the Add button, the key value will be displayed, copy, and save the value in a safe location.
- You’ll need this key later to configure the project in Visual Studio. This key value will not be displayed again, nor retrievable by any other means, so record it as soon as it is visible from the Azure portal.
- Type a key description (of instance
- Select the API permissions section
- Click the Add a permission button and then,
- Ensure that the Microsoft APIs tab is selected
- In the Commonly used Microsoft APIs section, click on Microsoft Graph
- In the Delegated permissions section, ensure that the right permissions are checked: User.ReadBasic.All. Use the search box if necessary.
- Select the Add permissions button
Step 3: Configure the sample to use your Azure AD tenant
In the steps below, “ClientID” is the same as “Application ID” or “AppId”.
Configure the pythonwebapp project
Note: if you used the setup scripts, the changes below may have been applied for you
- Open the
app_config.pyfile - Find the app key
Enter_the_Tenant_Name_Hereand replace the existing value with your Azure AD tenant name. - You saved your application secret during the creation of the
python-webappapp in the Azure portal. Now you can set the secret in environment variableCLIENT_SECRET, and then adjustapp_config.pyto pick it up. - Find the app key
Enter_the_Application_Id_hereand replace the existing value with the application ID (clientId) of thepython-webappapplication copied from the Azure portal.
Step 4: Run the sample
- You will need to install dependencies using pip as follows:
$ pip install -r requirements.txt
Run app.py from shell or command line. Note that the host and port values need to match what you’ve set up in your redirect_uri:
$ flask run --host localhost --port 5000
Community Help and Support
Use Stack Overflow to get support from the community.
Ask your questions on Stack Overflow first and browse existing issues to see if someone has asked your question before.
Make sure that your questions or comments are tagged with [azure-active-directory adal msal python].
If you find a bug in the sample, please raise the issue on GitHub Issues.
To provide a recommendation, visit the following User Voice page.
Contributing
If you’d like to contribute to this sample, see CONTRIBUTING.md.
This project has adopted the Microsoft Open Source Code of Conduct. For more information, see the Code of Conduct FAQ or contact opencode@microsoft.com with any additional questions or comments.
More information
For more information, see MSAL.Python’s conceptual documentation:
For more information about web apps scenarios on the Microsoft identity platform see Scenario: Web app that calls web APIs
For more information about how OAuth 2.0 protocols work in this scenario and other scenarios, see Authentication Scenarios for Azure AD.